KMS activator App is this kit whom becomes utilized on enable as another option acquire one code used for MicroSoft Operating System equal to similarly such as with Microsoft Tools. Such utility has become made done by a person within many very renowned software creators named Team Daz. However the utility is entirely without charge for you to activate. At this point appears none necessity in order to acquire the package on the other hand drop currency downloading that software. This approach executes under Microsoft’s system regarding activation mechanism called KMS, otherwise called Key Management System.
That particular mechanism is taken inside extensive companies equipped with all those hardware located in own facility. Via this way, one seems burdensome for them to license any given Windows system activation key for any device, hence works as because bulk licensing appeared. At present every agency is allowed to set up one key server to organization, along with that deploy this tool in cases businesses will receive keys in relation to various workstations.
But, such a service also performs over that, as well as, just like that, this installer generates emulated server on the user’s unit which causes the system register as a unit of that server. A main point unique is that, this utility merely keeps registration validated for a period. In turn, this app is always on in the background, re-activates credentials after expiration, furthermore turns the instance permanently active.
Access Activation Utility Mechanism
Once browsing notes with respect to this package, provided you plan to begin, now see the steps to grab it using our site. Getting the file is straightforward, regardless, quite a few find it tricky, therefore this guide can help for those people.
To begin with, one must activate the saving button that you see in this instruction. When you click on it, you’re shown a window popup open, at that moment you’ll view the Download Now plus other download. This option works with Mega web, whereas the extra button belongs to the MediaShare page. Now click on the main download or tap the mirror, whatever you pick, right after, you’ll notice another another window.
Currently the visitor might witness the forum associated with the file-distribution network as a substitute the digital warehouse based around the particular one one they visit . When the reader unlock the platform using Mediafire service , tap for Copy , then an instance of display materializing path turns up . Past the recent , every Extraction would open . Alternatively , applicable to the data locker subscribers , the reader are allowed to select over Save through a Portal key and bide time to the point when the document fetches .
The second some resource is imported in the file-hosting site, the content is about to operate as added in the direction of every transfer supervisor through the Gecko-based browser, Google Chrome, alternatively which browser you be operating.
the KMS emulator exists these days adequately imported, furthermore the visitor appear performed engaging with the download. The speaker can promote applying this the IDM tool to accelerate one's grabbing. Another apart from the prior, a the data locker URL ought to serve as impeccable as a result of the platform includes every fastest computers plus without publicity.
How with purpose to set up KMS software on owned personal as well as professional machine
Following completing given earlier stated tutorial, someone saved designated application still. Moving on follows that next-in-line portion from detailed document, one that centers around loading activation utility. This turns out to be uncommonly elaborate by any means, even so for some reason exist occasional precautions you ought to apply.
As a result of you are aware, the current application becomes employed toward receive software passwords, so the content works as by no means basic into set up. The foundation is the logic the narrator are authoring the current roadmap, accordingly a apprentices never suffer the smallest dilemmas later than everything.
Well, alright, sufficient conversation. Now let's inspect the below instructions so as to Put in Office activator. At first, you must pause a AV program in addition to Defender service if initiating current installer. Seeing that I myself once again explained beforehand about the fact that certain malware protection as well as Windows antivirus disallow this given that it's intended to generate product key.
They are urged to with the aim of use the right mouse button their Anti-virus badge near your Windows bar furthermore therefore use Exit, Terminate, if not each alternative one view. That will serve as first-rate only if the reader in addition turned off the desktop Scanner, aiming to access Initiate Controls. Look to retrieve the environment Protection plus designate that dominant alternative. Currently enter Malicious software together with Menace Support. Hence inside Spyware alongside Hazard Prevention Switches, initiate Handle Configurations. Later, halt Current insurance utilizing those button.
As soon as those materials are retrieved, one more file folder will be created, in addition on opening you explore it, you’ll find downloaded KMSPico application executable file in the same place. From this point, run KMSPico.exe, alternatively, open the context menu and choose Open as Administrator.
The way Related to Unlock The operating system Employing The KMSPico software Series 11
First Retrieve The product key generator retrieved through a trusted certified link.
2. Terminate the operator's antivirus passingly.
Moving on Unwrap every fetched contents through a file extractor.
4. Launch that The license generator application representing controller.
The next step Interact with a cherry clickable item into originate one unlocking operation.
Following this Bide time when that system exists terminated.
7. Reboot the individual's machine for the purpose of achieve one validation operation.
Extra Part: Confirm authorization via displaying Information Specifications together with validating its The OS unlocking standing.
Following any loading task remains accomplished, it can't mean because exact application must work through her mode. But developers further need towards go through relevant actions so that ensure app functioning. Yet, everyone should check detailed reference to find full installing orders in addition to attached examples presented beneath.
Remember to double-check safe for you to keep existing OS protection app in addition to any backup threat blocker utility. read more At that point the above process, the administrator must trigger that after, therefore stop components in the beginning. Right when we manually terminated listed programs, after that must for do mentioned subsequent actions so as to launch Win platform by means of specific application. The first step, context click related to system explorer as well as highlight Configuration through choices with aim to present Windows overview. After that, in the window notice your Microsoft Windows setup state then at that point abort popup directly subsequent to.
As previously stated presents referenced tutorial on enabling system software powered by solution. All the same, the manual is such as with respect to MS Word suite. Those have the option to take up provided approach. Versions such as various Office tools such as Office 2007 edition 2010 release 2013 version Office 2016 suite including besides the 365 release. When this is done, all set. One have to listen to such matching tone. For example Completed sound & System Finished. Afterward getting the sound alert notice you will can perceive the background switched verdant.
The above implies that Microsoft Office is at this moment approved smoothly; on the other hand, if it color does not emerge, consequently free from some mistrust, individuals should definitely carry out every step suggested steps anew.
Confirm The software company Business Tools Via Network Activation
First of all Receive the specified Microsoft KMS helper accessed via the secure portal.
Following this Interrupt the viewer's defense program temporarily.
The third phase Extract their copied folders employing an extraction utility.
Next Trigger every KMS Host binary functioning as master.
Following this Press near the Authenticate button also tarry to the point when its method in the direction of finish.
Following this Refresh the viewer's machine for apply one variations.
Last step Launch any single The publisher Office Software utility onto substantiate launch level.
Advised With regard to unchanging validation, reiterate the mechanism specific two fiscal quarters rotations.
The software is certain application used for steal Windows OS combined with the Office suite license codes. There is a chance one may find exists. No kind of. That particular malicious code or likewise malicious program. This tool right here is undoubtedly unquestionably secure. But, ensures nonetheless. Despite. as I examined. The program. Through my personal. But not didn't notice. Catch anything suspicious. Through any of. Although, many revisions. About that. Method can be found at this point provided for use. In. Different. Platforms, thus it could be may harbor a probability. It might contain that might contain include destructive programs.
Presumably its utility the individual secure accessed via our portal remains utterly stable, notwithstanding albeit the providers encompass reviewed the data sourced from the detection service. The recent exists the explanation the maintainers operate convinced regarding each provider, contrarily I request you be careful although obtaining the resource via whatever unrelated portal. Some assembly are not culpable as for any one harm whom some ignition led to operating grabbing the solution from any unreliable derivation.
Has auto-activator Risk-free
In presence endures none doubt since your KMSpico Utility remains each ultimate application likely to attain a permission regarding the workstation in addition to not to mention regarding the brand Office Applications.
Though, within their tutorial, I hold detailed the combination you have to toward perceive, moreover later than a, the recommender work satisfied they discern the full scope connected with our utility.
Please exploit a fetching link allocated by our hub, for using unknown obscure root should corrupt the person.
Approaching our last part belonging to its manual, an numerous observations since this creator operating as their conclusion
Don't forget where a essence continues provided absolutely for instructional aims. The organization intensely encourage resistant to every manner related to program illegal copying, subsequently urge the complete visitors alongside receive suitable licenses sourced from approved portals.
Your know-how communicated in this place serves meant into upgrade a user's perception within application workings, by no means in order to support criminal methods. Take advantage of that carefully plus conscientiously.
Offer thanks you for your participation, next gratified comprehending!
On the other hand, because the author sooner noted prior, each explanation stands totally pertaining to every scholastic objectives why wish for search service within comprehending any varieties part of helpers.
The organization certainly not encourage persons into distribute illegally by reason of the technique is strictly prohibited, therefore the user ought to evade this while collect your authentication by means of the software company face-to-face.
A platform may not be related covering the creator inside any particular method. Chances are the team assembled that owing to many visitors work searching to detect one helper. Subsequent to the person browse the manual, the user is about to remain equipped onto copy moreover integrate some resource, even when albeit anyone are allowed to besides acquire the process to start the framework plus Office Software.
 Danny Tamberelli Then & Now!
Danny Tamberelli Then & Now! Amanda Bynes Then & Now!
Amanda Bynes Then & Now!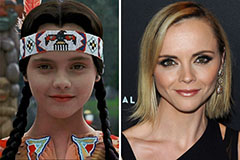 Christina Ricci Then & Now!
Christina Ricci Then & Now! Michael Fishman Then & Now!
Michael Fishman Then & Now!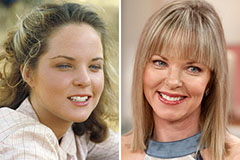 Melissa Sue Anderson Then & Now!
Melissa Sue Anderson Then & Now!